Hybrid Purple Teams

Summary
Penetration testing is an essential component of a robust security program and is required by some regulatory bodies and standards. However, there are several drawbacks associated with this type of security verification. First, it can be quite expensive, especially for organizations that require regular testing. Second, there is a shortage of skilled and experienced professionals in this field, making it challenging for organizations to find qualified testers. Third, a penetration test frequently presents an insufficient understanding because the tester typically ceases their examination upon obtaining complete access. Finally, penetration testing only provides a snapshot of the security status at a particular point in time and may not capture emerging threats or vulnerabilities that arise later.
To address these issues, the white paper presents a new approach that optimizes the use of existing resources while improving the overall security posture. This approach involves leveraging an autonomous penetration testing platform to perform some of the tasks typically performed by external penetration testers. By doing so, organizations can reduce the cost of testing while simultaneously improving the level of security.
The new approach also emphasizes the importance of continuous monitoring and assessment of the security status, rather than relying solely on periodic penetration testing. This ensures that emerging threats and vulnerabilities are identified and addressed promptly, reducing the overall risk to the organization. The ongoing tests also serve as a means of re-evaluating previously addressed vulnerabilities to ensure that they no longer pose a threat to the organization.
Traditional Types of Penetration Tests
There are several reasons for organisations to performing a penetration test:
- Identify vulnerabilities: Penetration testing can identify vulnerabilities that may exist in a system, network, or application that could be exploited by an attacker.
- Improve security posture: By identifying vulnerabilities, organizations can take steps to improve their security posture and reduce the risk of a successful attack.
- Meet regulatory requirements: Many regulatory frameworks require organizations to perform regular penetration testing to ensure compliance.
- Gain insights into security gaps: Penetration testing can help organizations gain insights into security gaps that may exist in their defences, such as weak passwords or unsecured network protocols.
- Test incident response: Penetration testing can also help organizations test their incident response plans and identify areas for improvement.
Overall, penetration testing can be an important component of a comprehensive security strategy and can help organizations identify and address vulnerabilities before they can be exploited by attackers.
Traditionally, there are several types of penetration tests:

Autonomous Penetration Tests
Recently, a new type has emerged. Autonomous penetration testing combines the benefits of automated penetration testing
- more frequent testing and
- lower costs and internal effort,
with those of manual penetration tests
- more complete coverage of the application and
- proven exploitability.
Autonomous penetration testing does not require credentials to start. It can chain together weaknesses like a skilled adversary and automatically generate attack trees to isolate the root cause of an exploit. This allows defenders to understand precisely what changes are needed to protect an application.
The tools providing these autonomous penetration test typically conduct the following steps:
- Reconnaissance
Any successful attack requires intelligence on the target. They start with unauthenticated access to the system, then create a Knowledge Graph, identifying all hosts, misconfigurations, open ports, and searches for credentials. - Maneuver Loop
They orchestrate many offensive tools to harvest credentials, exploit vulnerabilities, and exploit default settings and misconfigurations to execute attacks. - Verified Attack Plans
To simplify prioritization and remediation, results are provided as “Proofs” with graphical and textual representations of each step in a successful attack. This includes which tactics were used, which weaknesses were identified and exploited, how credentials were obtained, and the paths taken to gain privileges and access to systems. - Impact
They identify and report on data at risk across physical and virtual environments it was able to access with read/ write privileges, including SMB shares, NFS shares, FTP shares, cloud storage, vCenter servers, and databases. - Contextual Scoring
They evaluate and prioritize each weakness by its role in the successful attack – not by base CVSS score. Organizations can quickly identify those weaknesses that present the greatest threat and must be addressed immediately, and which can be safely deferred. - Actionable Remediation
They provide precise and actionable remediation guidance, allowing security and operations to resolve issues at the root cause quickly

An autonomous penetration testing platform offers a significant advantage over vulnerability scanners in terms of reducing the number of false positives and enabling context-based prioritization. These platforms are designed to report only the vulnerabilities that are genuinely exploitable, utilizing their knowledge graph to prioritize based on the risk of a successful attack.
Red + Blue = Purple
In cybersecurity, a "red team" and a "blue team" are two groups with different roles and objectives.
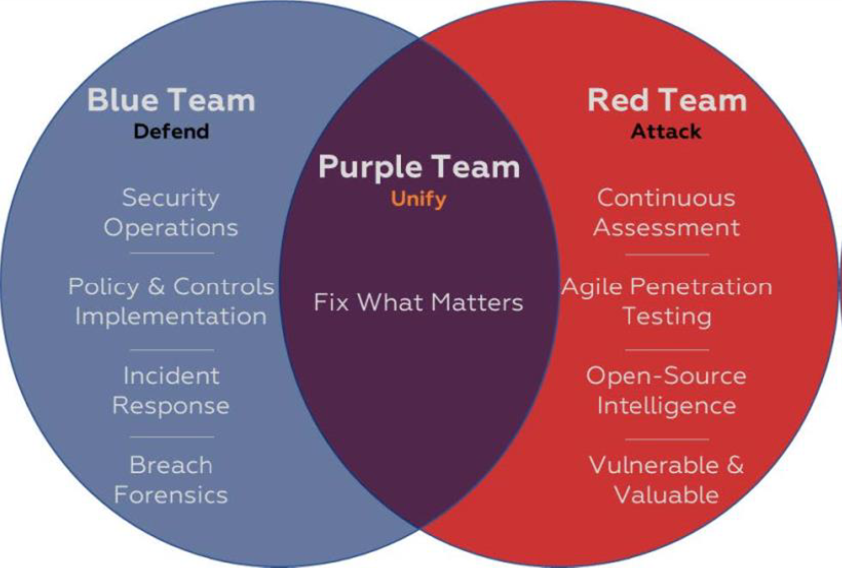
The Red Team's primary objective is to simulate a real-world attack against an organization's security infrastructure, applications, and networks. They use a variety of techniques and tools to probe for vulnerabilities and weaknesses in the organization's systems, often mimicking the tactics of real attackers. The red team typically works independently and tries to remain undetected, so they can provide an accurate assessment of the organization's overall security posture.
The Blue Team is responsible for defending the organization against cyber threats. They work to monitor and identify suspicious activity on the organization's networks and systems and respond quickly to prevent or minimize any damage from a successful attack. The Blue Team also works on maintaining the organization's security posture by regularly reviewing and updating security policies, conducting security training for employees, and implementing new security controls.
In summary, the Red Team tries to break the organization's security, while the Blue Team works to protect and defend it. By simulating attacks and responding to them, both teams can help organizations identify vulnerabilities, improve security measures, and develop effective incident response plans.
The concept of creating a purple team is rooted in the idea that teams can enhance their knowledge and skills by working collaboratively. By sharing insights and best practices, the teams can mutually benefit and bolster their cybersecurity efforts.
New Approach
Due to the lack of skilled resources, the role of a red team often involves hiring a human penetration tester. These penetration tests are only carried out every couple of months, sometimes even only once a year or after changes in the environment. While this process helps to identify vulnerabilities, the lack of a "Purple Team" can hinder progress. Without teams working together and learning from one another, there's a risk that some vulnerabilities will go undiscovered in the period between penetration tests.
And this is where the autonomous penetration tests come into play. They take over the role of the red team at a fraction of the cost and much more agile. The following graphic shows how this could look in practice:

The duration of vulnerability exposure decreases over time as identified vulnerabilities are addressed earlier, resulting in a reduced window of opportunity for attackers. Additionally, the blue team continuously learns from the red team, the autonomous penetration testing platform. This true purple team approach reduces the total effort for the blue team to fix vulnerabilities and significantly mitigates cyber risks.
Hybrid Red Team
Although some organizations rely solely on external penetration testers, others have already established an internal red team and already live a purple team approach. The adoption of an autonomous penetration testing platform does not require such organizations to fire their red team.
These platforms focus on the low hanging fruits, that – if not addressed – cause most of the risk. Instead, these organizations can utilize the platform to free up the resources of their red team for tasks that require human expertise. These tasks may include additional testing of high-criticality applications, penetration testing of non-standard environments such as OT or custom applications, and forensic investigations.
Conclusion
With the shortage of skilled manual penetration testers and the high cost of external penetration tests, organizations are compelled to reconsider their approach to verifying their security posture. One potential solution is the hybrid purple team model presented in this whitepaper, which offers a way out of the challenge of balancing frequent testing to mitigate risks with the availability of skilled resources.
Of course, a comprehensive strategy for risk reduction should take other factors into account. The approach must be integrated into mature processes for evaluating the criticality of assets and potential risks to the business. Additionally, fixing vulnerabilities is crucial, so blue teams must be adequately resourced to effectively reduce cyber risks.



